Why an App is visible to the user?
There are two reasons why an app is visible to a user:
- If the user is a maker i.e. the user has write/create privileges on Model-Driven App (AppModule) entity
- If one of the roles that is associated to the user, is also associated to the app.
Maker
If a user is has maker persona he basically has the rights to create new apps or do updates to any existing app. By default the OOB system-customizer and system-admin roles are considered to be maker-persona roles.
Since the maker can do an edit on any app, this user is able to see all the apps in the system.
Having the maker privileges on a user is the cause of the majority of visibility related issues. The customer complains why this user is able to see a particular app or all apps, without realizing that they have given that user the write/create privilege on AppModule entity.
The customer should be able to check this privileges himself by looking up the privliege levels of the roles associated to the user. Here is the public documentation which calls out this behavior of access to all apps:
Other Users
For a user to get an access to any app, he must have read privilege on the Model-Driven App entity through one of its associated roles, as shown below:
If the user doesn't have above privilege, he cannot get access to any app.
Now, say the user has read privilege on the Model-Driven app and the customer wants to share an app with that user. It can be done so by following steps mentioned in our public documentation to share a Model-Driven app here
Issues Addressed by App access checker:
App access checker tool helps to identify
- if an app is visible to the user or not.
- Reason why app is visible or not.
- If user has required license or not.
- To have an access to the app, user should have
- create / edit privilege on app module
- read privilege + role association
- read privilege + team association with user + team associated with role
- For sales and svc apps, user must have license assigned as well
How to use App access checker.
- Admin / Customizers can use this tool to search apps based on userid / email address.
- Launch this diagnostics page in your browser by typing <orgURL>WebResources/msdyn_AppAccessChecker.html
- Enter UserId or email address in Search Field
Example 1
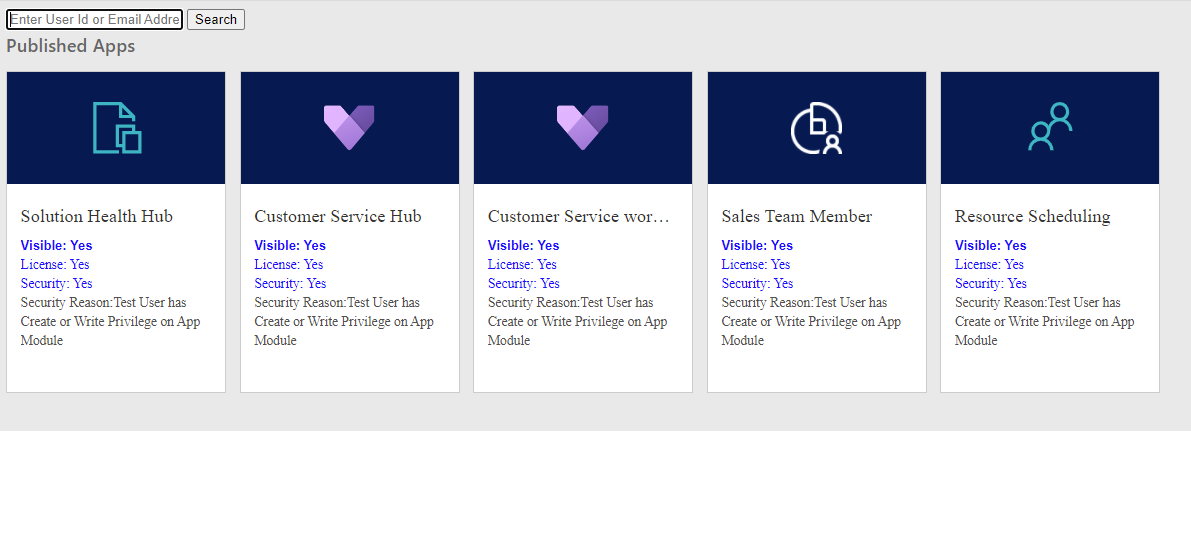
Example 2
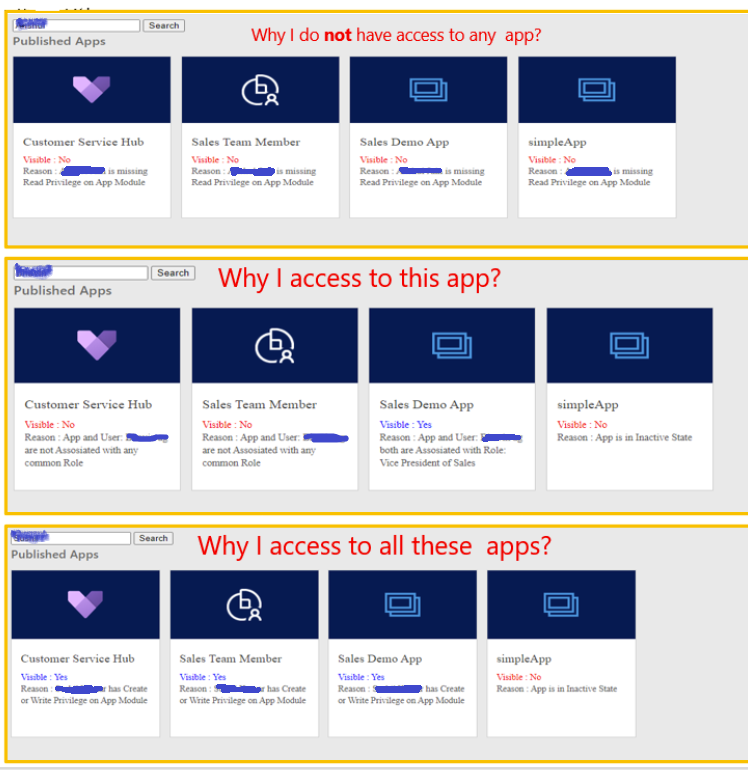
NEW!: Licensing Information has been recently added to this tool.
To get Licensing Information, the user must have the required security privilege for the app.
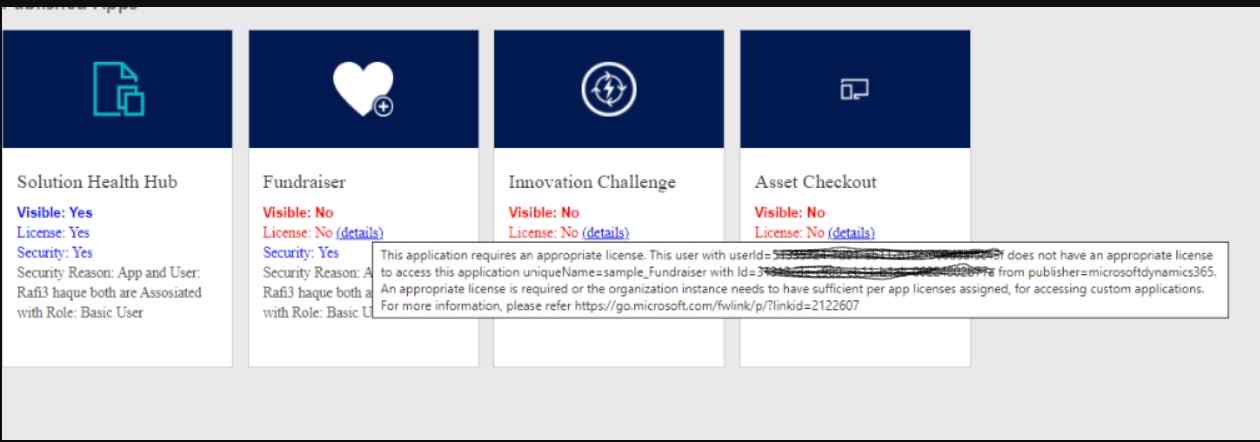
Example 1
In this example, the user has the required security privilege for the app but does not have the required license to access the app.
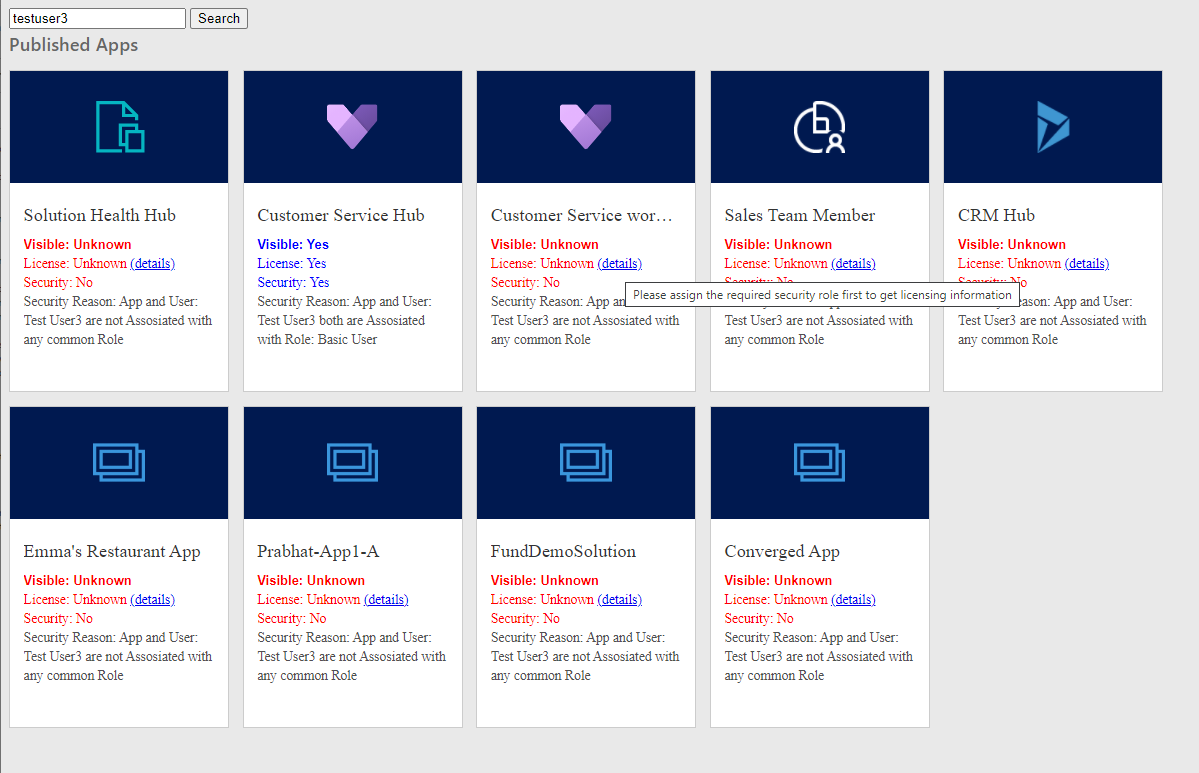
Example 2
In this example, the user does not have the required security privilege, so this tool is not able to show licensing details.
How to interpret results
- If user doesn't have read privilege on Model- Driven Apps, None of the apps will be visible to user.
- If user have Read or Write Privilege on Model-Driven Apps, then All the apps will be visible.
- If Page shows that User and App are associated to any common roles and if you notice that User is not associated to that role, then Please check if user is part of any team and if that team is associated with that role.
Limitation
- It will not show Details for Outlook App as Outlook app is visible to only administrators.
Tips
- You can troubleshoot mobile app access issue as well - Check if App is visible in browser to rule out any role/access configuration issue
- You can impersonate another system user in a support instance. This is really helpful in investigating visibility related issues and knowing what user is seeing in /apps page.
Share a model-driven app using Power Apps - https://docs.microsoft.com/en-us/powerapps/maker/model-driven-apps/share-model-driven-app
App Module/Model driven app FAQ - https://docs.microsoft.com/en-us/powerapps/maker/model-driven-apps/model-app-faq



